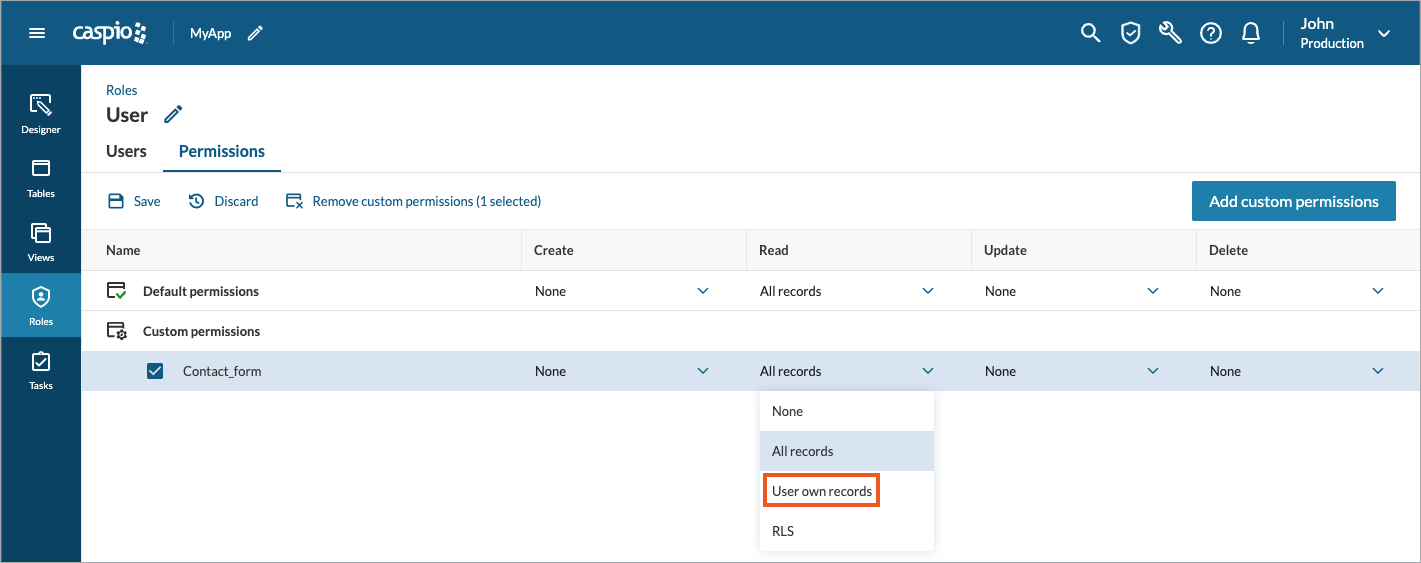
You can restrict access permissions to data exposed in an application only to the users who own a record. It can be achieved with the User’s own records option that limits access to table records based on the field that stores the user’s ID. For example, you can grant users editing permissions to all the orders that were created by them. Or, in a ticket management app, you can limit access to support tickets only to their creator, based on the user ID captured in each record.
Access to user's own records can be configured with any compatible directory field supporting the following field data types: Text (255), Text (64000), and GUID.
Setting Role Permissions Based on Record Ownership
The following example includes a table that stores support tickets and the User application role, which specifies that users can view and modify only the tickets that they created. A user can create new tickets but cannot delete any tickets.
You can also use this tutorial to set up role permissions when records are assigned to directory users with a table field that identifies the user.
Steps
- Create the User role for the “Support_portal_tickets” table.
- Configure the permissions for the role.
For example, you can configure the User role to allow users to create new tickets but view and edit only the tickets created by them, without the option to delete any tickets: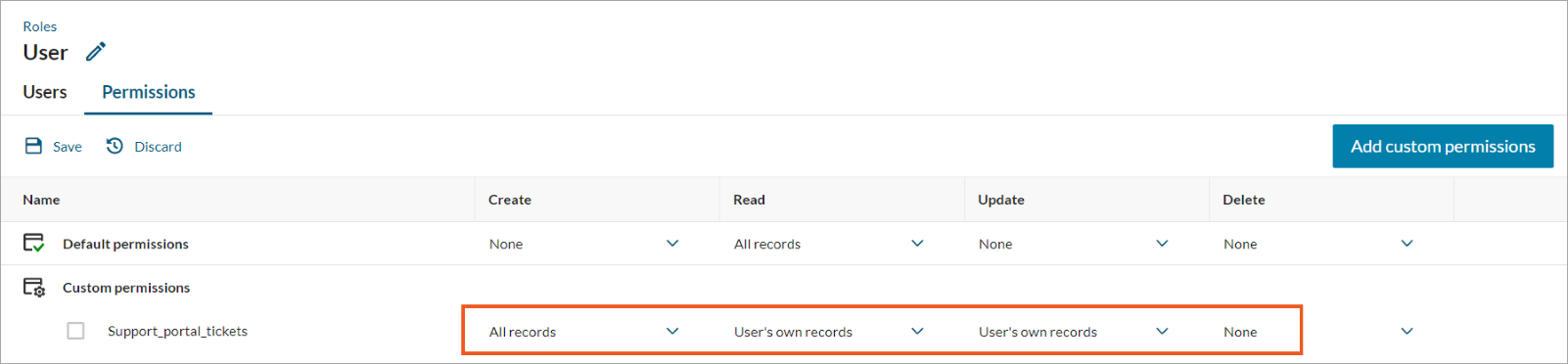
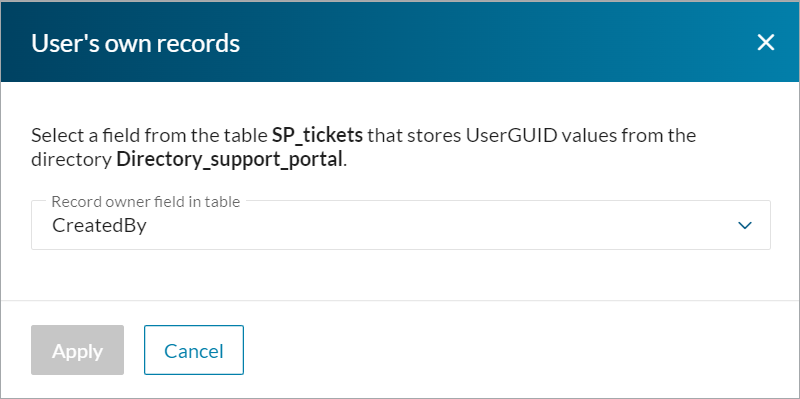
You can configure this behavior with the User's own records option, by selecting the field that stores the ID of the record creator:
Learn more about how to use application roles to restrict access to records that are stamped with a user ID.

